Configuring SNMP in a VMware vCSA
In this article, we’ll review the necessary information for how to configure SNMP v1 options in a VMware vCenter Server Appliance. If you’re reading this article, you likely already know what SNMP is, as well as how to utilize it. If not, let me at least give you a brief intro, stating what it is and what it’s used for. If you’re already familiar with SNMP, skip ahead to Configuring vCenter SNMP Options.
1. SNMP Introduction
SNMP (Simple Network Management Protocol), as the name already indicates, is a network protocol (particularly an “application layer” protocol in the OSI networking model). In a nutshell, it’s used to “get” information from networked devices and/or to “send” information from one networked device to another.
“Why would I use this protocol?” you might ask. There are way too many examples to name, but I’ll list a couple of basic examples to help you become more familiar with why you might use SNMP.
Example 1: Where I work, I utilize a free piece of software called Spiceworks. One of the features of this software is that it can query various devices on our network (switches, firewall, printers, etc) in order to “get” information about them. Spiceworks utilizes SNMP to query all of the available information from each networked device that it communicates with.
Example 2: We also have a centralized syslog server (Kiwi) that we “send” device information to; mostly event logs from our switches and firewalls.
Now that I’ve reviewed what SNMP is, and you’ve seen a couple of examples for how it can be used, let’s look at how to configure SNMP in a vCSA. The first thing you need to do is verify that you have appropriate access to the server (which will require enabling SSH).
2. Verify that SSH is enabled
In order to verify this, you need to login to the admin web console of the vCSA. This can be done by navigating to the following address via a web browser (substituting “<server_hostname>” with your appropriate server name):
https://<server_hostname>:5480/login.html
Login with the appropriate admin credentials and verify that SSH is enabled. The default landing page in the web console is the “Summary” page. To verify that SSH is enabled, click on “Access” in the menu at the left, then verify that “SSH login” is set to “Enabled”. Refer to Figure 1 below:
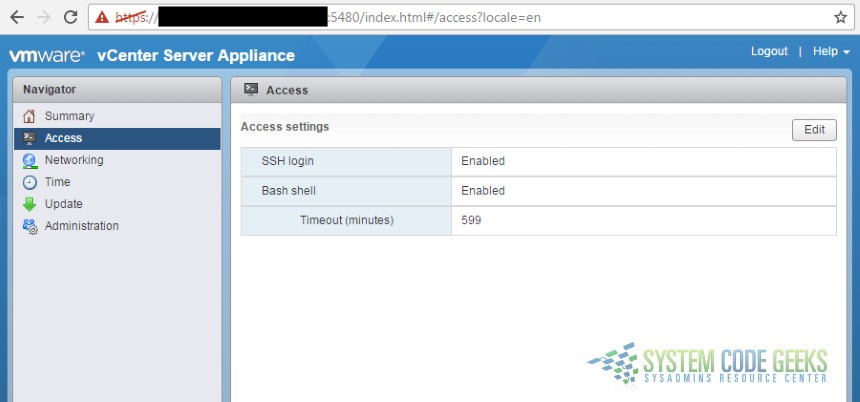
Now you’re ready to access the server via SSH and verify that you have appropriate shell access.
3. Verify appropriate shell access via SSH
I won’t go into detail about how to SSH into your server, but I’ll at least mention the free SSH client that I use: PuTTY.
There are two types of shell prompts that you can utilize when managing a vCSA via an SSH session: “BASH” or “appliance”. Once you’ve successfully connected to your server, you’ll be starting your management session from whichever one of these shells has been set as the default. When you’re at an appliance shell, it will look like what you see in Figure 2 below:
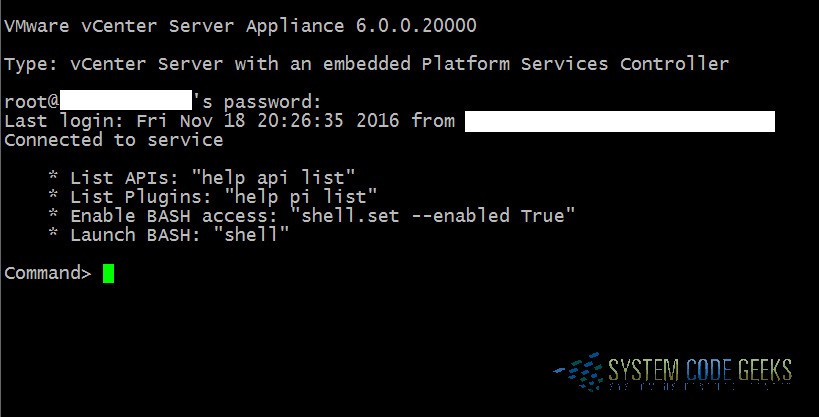
If your prompt looks like what you see in Figure 2, you are already at the correct prompt and are ready to proceed to step 5!
If your shell prompt does not look like the picture in Figure 2, then your server has been configured to use BASH as the default, which would look like this:
<server_name>:~ #
If you’re at a BASH prompt, proceed to the next step in order to change the default shell.
4. Enabling the appropriate shell access on the server
If your SSH session defaults to a BASH prompt, you’ll need to change it so that it defaults to the appliance shell. This can be done by typing the following command:
chsh -s /bin/appliancesh root
After typing the above command, the only way to access the new default prompt is by logging out of your SSH session and logging back in. This can be done by simply typing:
logout
NOTE: As stated above, after changing the default shell from BASH to appliance, a logout is necessary in order to successfully access the appliance shell at the next logon session.
After you re-establish your SSH session and you’re at the appliance shell, you’re ready to start configuring the SNMP options!
5. Configuring vCenter SNMP Options
There are various SNMP options that can be configured, including ones that utilize extra security options, but as stated in the introduction of this article, I’ll be covering the options involving SNMP v1.
NOTE: SNMP v1 (instead of v2 or v3) is the easiest to setup because it only requires the most basic of communities (“public”). However, it’s the least secure version of SNMP since it doesn’t utilize authentication or any privacy controls. With that said, if someone with true hacking skills has access to your network, SNMP configurations will likely be one of the least of your concerns.
To check the current SNMP configuration at any time (either before or after making changes), you can type:
snmp.get
You will see output similar to what’s displayed in Figure 3 below:
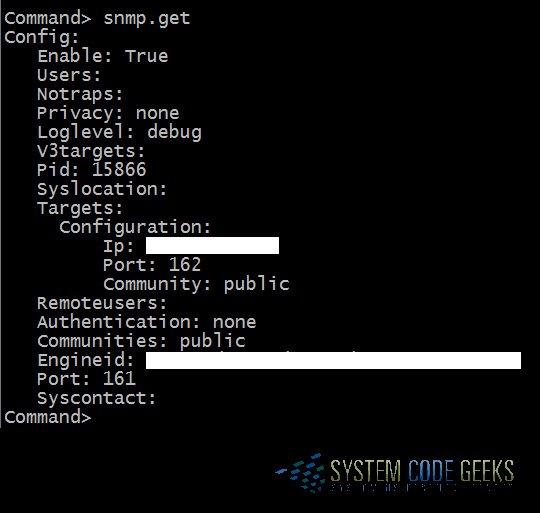
5.1 Create an SNMP community
Before SNMP can even be enabled, the first thing you need to do is create a “community”. Since we’re using SNMP v1 in this article, we’ll create the default community of “public”. To do this, type the following command:
snmp.set --communities public
5.2 Configure an SNMP trap
In the environment where I work, we have our vCSA configured to send SNMP trap data to our Kiwi syslog server. If you’d like to configure a trap for your vCSA to send its SNMP data to, this can be done by typing the following command (substitute <trap_server_ip> with your appropriate trap server’s IP):
snmp.set --targets <trap_server_ip>@162/public
NOTE 1: SNMP uses the default UDP port 161 for general SNMP messages and UDP port 162 for SNMP trap messages.
NOTE 2: You can add multiple targets as well, separated by commas. Here’s an example:
snmp.set --targets <server_ip_1>@162/public,<server_ip_2>@162/public
5.3 Configure the logging level
NOTE: There are four levels of logging to choose from: debug|info|warning|error (“debug” has the highest level of verbosity, and “error” has the lowest).
Set the logging level using the following command:
snmp.set --loglevel debug
5.4 Enable SNMP
It’d be crazy to configure all of this and not have SNMP enabled, so make sure that it’s enabled by typing the following command:
snmp.enabled
5.5 Send a test trap
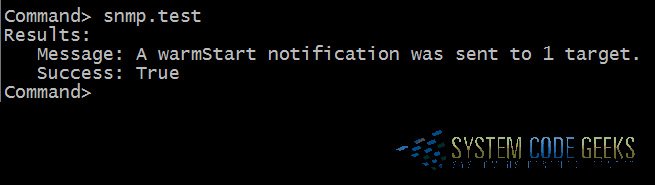
The last thing left to do is to send a test trap to verify that the agent is configured correctly:
snmp.test
You should see something similar to this if it was successful (see Figure 4 below):
6. Summary
As you’ve hopefully learned from this article, first-time SNMP configuration options in vCenter are not as hard or as complicated as they may initially seem. It does however require understanding the basics of what SNMP can be used for, how to effectively manage your vCenter server via SSH and the GUI web console, and how to properly leverage commands from the appliance shell in order to successfully configure vCenter SNMP options.



BTW, the order of the commands to configure does not matter.
Would not recommend keeping the service logging at debug, the warning level should be sufficient.
I would lastly recommend configuring SNMPv3 only as SNMPv1/v2c are insecure.
see: http://blog.epijunkie.com/2015/03/enable-snmpv3-on-vmware-vcsa-6-0/
for example.
Thanks for the feedback Michael 🙂
5.4 Enable SNMPIt’d be crazy to configure all of this and not have SNMP enabled, so make sure that it’s enabled by typing the following command:
1
snmp.enabledyou made a mistake
the correct option snmp.enable